When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
Furthermore, it requires no interaction on the victims side.
Threat actors could use it to repeatedly crash vulnerable systems.
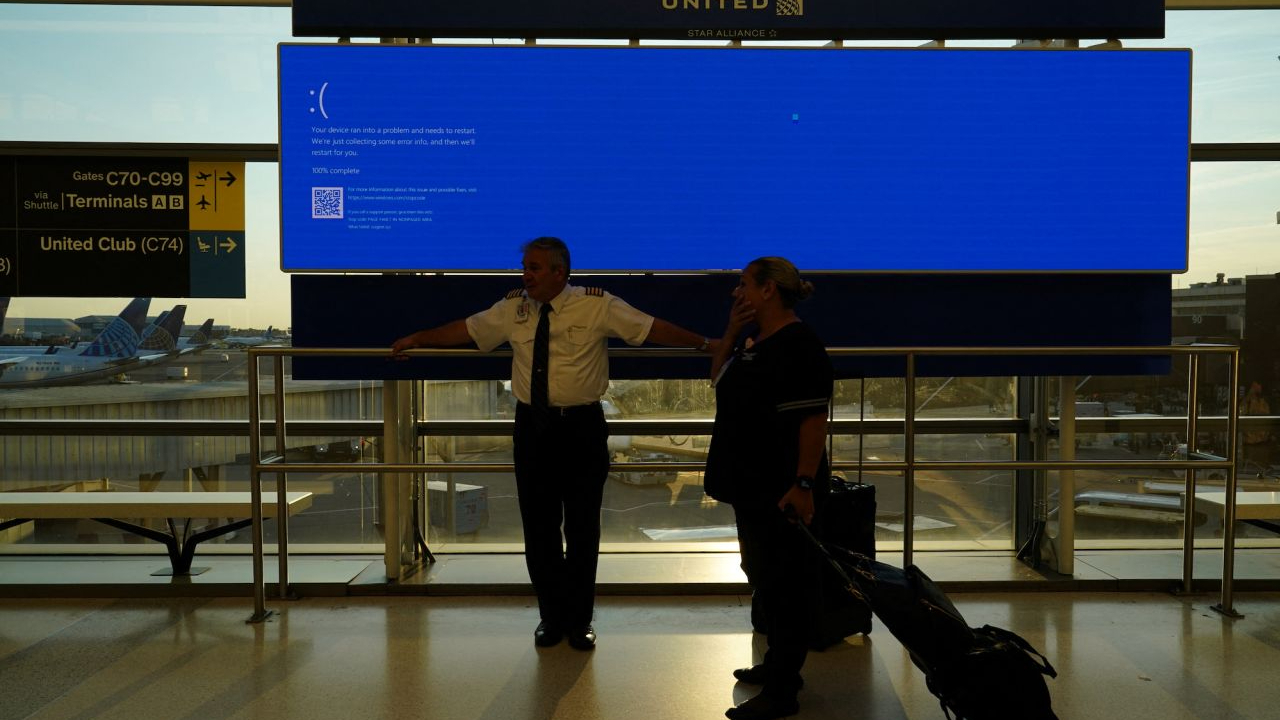
There is currently no evidence of the vulnerability being exploited in the wild.
However, it can be run with low privileges, making it available even for beginner attackers.
Fortras advisory also suggests thatMicrosoftis yet to address the issue.