When you purchase through links on our site, we may earn an affiliate commission.Heres how it works.
Encrypt your communications and online activities: you’ve probably heard these privacy-boosting tips before.
If you have enough metadata you dont really need content."

NymVPN has recently launched itsfree VPNversion in beta andlooks for testers.
Claudia Diaz has known about the extent of metadata surveillance for a long time.
“More specifically, I worked onmix networks,” she told me.
NymVPNis the first piece of software to use the mix internet infrastructure.

NymVPN has recently launched itsfree VPNversion in beta andlooks for testers.
What is metadata?
Diaz describes metadata as a letter in an envelope.
This is whatencryptionguarantees for all of your online communications and activities and it’s also known asend-to-end encryption.
The message is only one part of the process, though.
A letter is marked with the sender’s name and needs another name and address indicating its target destination.
Put simply, “Metadata includes everything about the data that is not the content.”
NymVPN has recently launched itsfree VPNversion in beta andlooks for testers.
Yet, the data packets executing your online activities leak metadata, too.
How many bytes, the patterns they move to, timestamps, and so on.
As Diaz says, it’s like the difference between what you say and how you say it.

Yet, controlling your body language is a lot harder.
These details can, however, be recorded and analyzed to assume what you don’t want to say.
Metadata speaks the language of computers: strings of code, letters, and numbers.
This makes it even easier to look for patterns, aggregate, analyze, and extract intelligence.
“Not only are these data exposed by default in the internet protocols,” she told me.
Yet, according to Diaz, even a normal VPN would not protect you against traffic analysis.
“That’s better,” said Diaz.
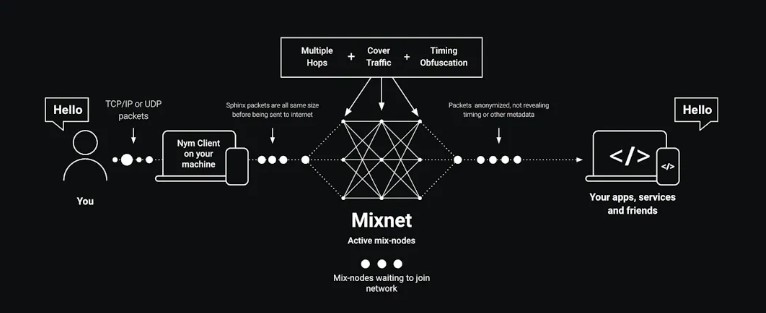
By making delays and covering traffic, Mixnet raises the bar even more."
This is the key word to understand the concept of Mixnet.
The real revolution of Mixnet is in the way it processes different data packets entering the server.
These include data fragmentation, dummy data packets, timing delays, and data packet shuffling.
He said: “AI models collect a lot of data by finding some patterns in the data.
Our VPN does the reverse.
We add fake traffic, we mix traffic up, and we scramble the pattern.”
Users will hide in the crowd the larger, the better.
What’s next?
Injecting covered traffic and reshuffling data packets comes at the cost of performance, however.
The more noise the web link is, the slower the internet connection will be.
This is why NymVPN operates on a fully decentralized infrastructure.
casein which companies have handed over users' data under court orders despite their no-log claims.
Alongside Claudia Diaz, also Harry Halpin was involved in the project.
Nym has now more than 200 active decentralized nodes.
The goal is to grow a community of professional people dedicated to running these independent nodes.
She said: “Metadata is this abstract and unconscious thing.
It’s then so much harderto raise awareness about it with users.
That technology allegedly now exists and is moving its first steps into the consumer world.